February 28, 2012
EU Court of Justice: Social Networks Can’t Be Forced to Monitor and Filter to Prevent Copyright Infringement
The SABAM v. Netlog decision follows a landmark ruling by the ECJ in the SABAM v. Scarlet Extended case in November 2011, where the Court held that a Belgian ISP (Scarlet) could not be required to adopt a system to filter and block the transfer of potentially copyright infringing music files on its network. In that case, the Belgian copyright collective management organization SABAM had obtained an injunction (a court order) against the ISP, requiring it to install a system that would filter all of its users’ communications for potential copyright-infringing material.
Yesterday’s ruling also involved SABAM. It had sought a similarly broad injunction against Belgian social media platform Netlog. The 2001 EU copyright directive mandates that copyright holders be able to obtain injunctions against intermediaries whose services are used by third parties to infringe copyright, but that is bounded by other EU obligations, including protection of citizens’ fundamental rights. The ECJ was asked to rule on the permissible scope of these injunctions, given their impact on Internet users’ fundamental rights and online service providers’ businesses.
The ECJ found that forcing Netlog to install a filtering system that would identify and prevent its users from making available any potentially copyright infringing files would require “active observation” of Netlog’s users. Following the 2011 SABAM v Scarlet decision, it held that implementing such a system would fall afoul of the key principle in Article 15 of the EU e-Commerce Directive, which prohibits EU member states from imposing a general obligation on ISPs and hosting services to monitor information they transmit or store, or to actively seek facts or circumstances that indicate illegal activity.
The Court also criticized the injunction on a second basis. In the 2011 Scarlet ruling and the 2008 Promusicae v. Telefonica decision, the ECJ held that in adopting measures to protect copyright holders, EU member states and courts must strike a fair balance between the protection of copyright, and the protection of the fundamental rights of individuals and businesses who are affected by those measures. The Court found that the filtering system being sought by SABAM required the identification, systematic analysis, and processing of information connected with the profiles of Netlog’s users. This would violate Netlog’s users’ right to protection of their personal data, enshrined in Article 8 of the Charter of Fundamental Rights of the EU. In addition, because the filtering system could not effectively distinguish between lawful and unlawful content, it could block lawful content, and undermine Netlog users’ right to receive and impart information protected under Article 11 of the Charter.
Given the protection required of citizens’ fundamental rights under the Charter of Fundamental Rights, the ECJ concluded that courts in EU countries can’t issue injunctions against hosting service providers that require them to install a filtering system with features as broad as the one in this case which (a) was directed at information stored on the hosting platform’s servers by its users, (b) applied indiscriminately to all its users, (c) was installed as a preventative measure (requiring hosting services to decide whether content is infringing), (d) was at the sole expense of the hosting provider, and (e) for an unlimited period of time.
So what does all this mean? Here’s a couple of our thoughts.
The ECJ ruling is directed at EU member countries, but it will have significant implications for the future of the global Internet. Injunctions are one of several strategies that intellectual property rightsholders have been pursuing to force Internet intermediaries to become copyright police. In countries around the world, IP rightsholders have used injunctions to impose filtering, blocking and user termination obligations on Internet intermediaries. These efforts are likely to expand under ACTA, because it requires signatory countries to make available broad injunctions to IP rightsholders, including temporary injunctions while a case is pending. By precluding pre-emptive filtering and blocking injunctions, the SABAM v. Scarlet and SABAM v. Netlog rulings set an important limit on this strategy for EU countries.
Because injunctions are issued by courts, usually after a process of weighing up all affected parties’ interests, measures imposed in this way theoretically provide better protection for Internet users than those adopted in private party voluntary agreements such as those we’ve seen in Ireland and Belgium. As we’ve noted elsewhere, Internet intermediaries are not competent to make legal determinations about whether particular content or conduct infringes copyright. Copyright holders’ efforts to require Internet intermediaries to take on this role under the guise of greater “co-operation” raise serious concerns about due process, transparency and accountability, and online free expression. In that respect, we welcome the ECJ’s clarification on the scope of injunctions available under EU law.
At the same time, we recognize that the ECJ’s Scarlet and Netlog decisions will now lead to increased lobbying pressure from rightsholder groups to change EU law, perhaps as part of the European Commission’s review of the 2004 Intellectual Property Rights Enforcement Directive. Let’s hope that EU policymakers approach this in as thoughtful and balanced a way as the ECJ.
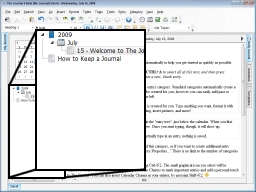 As you create new entries, you will see them listed in the “entry tree”, just below the calendar. When you first bring up a new entry date, it won’t be listed in the tree. Once you start typing, though, the entry will show up.
As you create new entries, you will see them listed in the “entry tree”, just below the calendar. When you first bring up a new entry date, it won’t be listed in the tree. Once you start typing, though, the entry will show up.